The newly discovered vulnerability is in the bash shell used by CGI and is dubbed "Shellshock" . The vulnerability enables easy upload and execution of code in many systems. The vulnerability is already being used maliciously to launch a kernel exploit with a connection to a Command and Control (CnC) server. Early estimates are that as many as 500 million computers and devices are vulnerable.
All embedded systems using CGI may be at risk. The vulnerability is believed to have a much bigger impact than the OpenSSL heart-bleed bug discovered earlier this year and may cause security breaches for years to come. In particular, embedded systems that are not easy to upgrade and some deployed devices may never receive a fix. The only solution and protection for consumers may be to purchase new equipment when this vulnerability is fixed.
The security problems associated with CGI
Envision that your objective is to create a water container. To meet this criteria the natural selection would be to start with something that may resemble a bucket. When we compare CGI in analogy, the solution provides a starting point which is equivalent to that of a strainer. Consequently, the application developer must spend a considerable effort identifying and sealing all of the holes of this strainer (CGI).
Unfortunately, CGI has no inherent or native security built into its structure, and with its many vulnerabilities, it creates a struggle to maintain such a solution in today's IoT generation of devices. Manufacturers are becoming increasingly aware of these problems, but usually as a casualty of consequence in the daily news rather than the advanced step to negate avoidable liabilities.
CGI has a long history of vulnerabilities. We have covered a few of these vulnerabilities on our CGI vs. LSP comparison page.
Lua Server Pages to the Rescue
Like CGI is the strainer, LSP in analogy, is the bucket, and is by design secure. Since there is no direct coupling between LSP and the shell in the operating system, one cannot use an exploit to run arbitrary code in the operating system's shell such as one can with CGI. The CGI security problems are irreparable. The best remedy is for device manufacturers to ditch the use of CGI and move to a much more secure model such as our Lua Server Pages (LSP) technology.
Real Time Logic serves the market to provide reliable web-enabled secure device technologies.

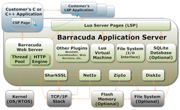 Das Plug-In basierte Barracuda Embedded Web Server SDK vereinfacht und
Das Plug-In basierte Barracuda Embedded Web Server SDK vereinfacht und  SharkSSL ist sehr Speicherplatzsparend, das Transport Agnostische API macht die Verwendung in jedem embedded System möglich, egal ob 8-Bit oder 64-Bit Mikrocontroller werwendet werden.
SharkSSL ist sehr Speicherplatzsparend, das Transport Agnostische API macht die Verwendung in jedem embedded System möglich, egal ob 8-Bit oder 64-Bit Mikrocontroller werwendet werden.