Want to learn how to exploit MQTT using Lua? I hope not. But maybe you want to learn how to protect yourself again the exploit... not a bad idea to start from the inside out.
MQTT is a publish/subscribe protocol that has gained popularity as an IoT protocol. MQTT clients connect to a broker which is in charge of exchanging the messages sent between the connected clients. MQTT includes many features that may leave the MQTT solution open to hackers. In this article, I will show you how easy it is to find unprotected MQTT brokers on the Internet and how to eavesdrop on all messages exchanged via the unprotected brokers.
Lua is an easy to learn, fast, and very powerful programming language used standalone and embedded into many programs. It is particularly popular in the gaming industry since it helps reduce the development time of complex game logic. Lua is also gaining in popularity in web development, and several web frameworks support Lua. The MQTT exploit is designed in HTML, JavaScript, and Lua. The MQTT exploit code listed below can be copied and run on an online public Lua web server. The following video shows a screen recording of the MQTT exploit code running on the public server.
Here you can read the complete article at dzone.com about this topic.
After all of the IoT security incidents surfacing in 2016, we have compiled a video showcasing how our new MQTT client for Lua subscribes to unprotected MQTT brokers on the Internet.
Watch the Video here and on YouTube:
Let's start 2017 right by not being oblivious to security.

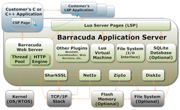 Das Plug-In basierte Barracuda Embedded Web Server SDK vereinfacht und
Das Plug-In basierte Barracuda Embedded Web Server SDK vereinfacht und  SharkSSL ist sehr Speicherplatzsparend, das Transport Agnostische API macht die Verwendung in jedem embedded System möglich, egal ob 8-Bit oder 64-Bit Mikrocontroller werwendet werden.
SharkSSL ist sehr Speicherplatzsparend, das Transport Agnostische API macht die Verwendung in jedem embedded System möglich, egal ob 8-Bit oder 64-Bit Mikrocontroller werwendet werden.